 By Trenton Baker, Senior Product Marketing Manager, KeepItSafe
By Trenton Baker, Senior Product Marketing Manager, KeepItSafe
Twitter: @keepitsafe
Since the Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996, there have been notable advances in protecting the privacy of patient information handled by healthcare plans, health care clearinghouses and certain types of healthcare providers. Unfortunately for patients and providers, technology and the many advantages of the cloud, including its scalability, cost-efficiency, and flexibility have continued to outpace legislation.
While the cloud makes file storage and sharing comfortable and convenient, its security risks are significant enough to have pushed for the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009. This regulation covers any service provider who has access to protected health information (PHI) including subcontractors who create, receive, maintain or transmit PHI on behalf of a business associate, including cloud providers.
This is serious business. The U.S. Department of Health & Human Services enforces HIPAA. HHS reported that in early 2018, Fresenius Medical Care North America agreed to pay $3.5 million to settle potential HIPAA violations. Moreover, in late 2017, 21st Century Oncology settled for $2.3 million to HSS. It is interesting to note that declaring bankruptcy does not let organizations skirt non-compliance fees as 21st Century Oncology had declared bankruptcy earlier that year.
It is evident that HIPAA-HITECH firmly regulates how the healthcare industry collects, stores, communicates and transmits protected health information. For healthcare organizations, compliance can be a major concern when deciding what to look for in a cloud-storage service provider.
HIPAA and Electronic Data Protection
HIPAA places additional requirements on protecting electronic PHI (ePHI), specifically the Security Final Rule’s Data Backup and Disaster Recovery Specifications that require:
- Secure backup “retrievable exact copies of electronic protected health information.”
- Frequent date backup. Frequency is proportional: no one expects you to backup aging Word documents every hour on the hour. However, you should set aggressive RPOs for applications where data loss is a significant event.
- Backed up data must be recoverable, the pivotal phrase being “restore any loss of data.” Excuses will not fly with HIPAA regulators and can lead to steep fines.
- Secure data-in-transit during backup and restore, and encrypt data-at-rest.
- Backing up data to a secure remote data center. HIPAA requires specific physical safeguards for HIPAA compliance including buildings that are hardened against natural and environmental disasters, and protection against physical and digital intrusion.
- Document all policies and procedures related to your backup, recovery, and disaster recovery, and periodically test them.
A Match Made in the Cloud
These requirements can be a significant burden on backup admins and disaster recovery managers. Many of them choose to invest in HIPAA-compliant backup as a service (BaaS) and disaster recovery as a service (DraaS) to simplify and improve HIPAA compliance. (It doesn’t hurt that organizations can also save money on capital purchases and high operational expenses.)
However, watch out—many cloud service providers (CSP) will say that they are HIPAA compliant, but does that mean they automatically meet your compliance needs? Maybe, maybe not. If they say, they are HIPAA-HITECH compliant, which primarily means their data center complies with facility and digital security regulations. Nonetheless, compliance goes beyond compliant infrastructure and encryption.
The Covered Entity (that would be you) and Business Associate (that would be your cloud provider) sign Business Associate Agreements (BAA) that align your partnership with HIPAA requirements. If the CSP is only willing to sign their boilerplate BAA, that may not be enough for your needs. Does your provider offer a detailed assessment of compliance gaps? Are they willing to customize SLAs in addition to signing the BAA? Also review the service provider’s HIPAA-HITECH compliance record as well as their availability, security, and performance metrics.
Encrypting your ePHI Data
Encrypting your cloud data is not just to prevent hackers from gaining unauthorized access to the data, but depending on the data in question, it is likely a requirement to comply with privacy laws such as HIPPA, PCI-DSS, FINRA, and soon GDPR. One essential element of encryption is the lack of existing CSPs that adhere to security best practices, not to mention the regulations that call for data at rest to be encrypted no matter where it resides. You guessed it one of the challenges of implementing data at rest encryption is that the most popular SaaS application and megacloud providers do not encrypt your data while at rest.
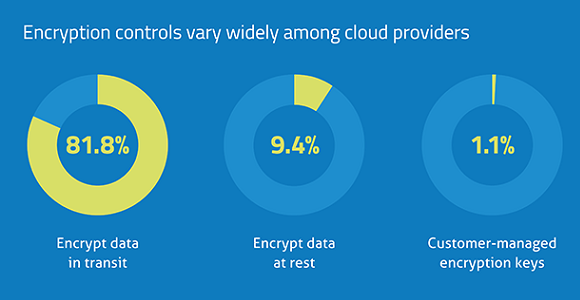
”Only 9.4% of cloud providers encrypt data once it’s stored at rest in the cloud, leaving it vulnerable to unauthorized access and data breaches.” – Source: Skyhigh Networks
Since adherence to regulations calling for encryption of data at rest in the cloud lies at the feet of the customer, not the cloud provider, it is wise to conduct your due diligence. If you are unsure what form of encryption is protecting your regulated cloud data, don’t hesitate to contact your cloud provider. Go ahead and make the call to ask what sorts of encryption they provide, if any, for cloud-based data protection. Ultimately, you are the one left holding the compliance bag.
Storing sensitive data at rest in the cloud can bring inherent risks specific to cloud deployments. Cloud data at rest risks can include:
- Malware
- Malware and/or Ransomware could conceivably access any non-secure sensitive cloud data and exfiltrate or lock data files for future extortion.
- Malicious Insiders
- Mischievous actions from non-authorized organization insiders could access data and exfiltrate it at their leisure.
- Cloud Leakage
- Cloud leakage can occur in some megaclouds where a virtual machine can compromise another cloud instance on the same physical server. This was exacerbated by the Meltdown/Spectre vulnerabilities, publicized in Jan. 2018.
- Loss of Physical Control
- Cloud providers tend to offer always-on SLAs. However, physical servers are taken offline for repair or replacement thus allowing for sensitive data to potentially walk out the door.
This article was originally published on the KeepItSafe blog and is republished here with permission.
