 By D’Arcy Gue, VP, Industry Relations, Phoenix Health Systems
By D’Arcy Gue, VP, Industry Relations, Phoenix Health Systems
Twitter: @DarcyGue
A HIPAA-related bomb hit the healthcare industry this summer. The Office of Civil Rights slapped a landmark penalty on a business associate – to the tune of $650,000. This was the first ever penalty on a business associate and gives sharp teeth to the 2013 Omnibus HIPAA Rule provision that HIPAA business associates are now equally subject to penalties for privacy and security breaches as providers and payors. What is most unnerving is how relatively minor the causative incident seems and how easily other business associates (and their covered entity clients) could be similarly penalized.
In a nutshell, in 2014 an unencrypted smartphone without password protection was stolen from the non-profit Catholic Health Care Services of the Archdiocese of Philadelphia, exposing information on 412 patients at six nursing homes. CHCS provided management and information technology services as a business associate.
OCR noted that at the time of the incident, CHCS had no policies for secure management of mobile devices containing PHI or for what to do in the event of a security incident. CHCS also had no risk analysis or risk management plan, which are required by HIPAA. According to Data Breach Today, data on the stolen iPhone “was extensive, and included Social Security numbers, information regarding diagnosis and treatment, medical procedures, names of family members and legal guardians, and medication information.”
Data breaches are rampant among business associates today. We reported earlier this year from a Ponemon survey: “87% of BAs have experienced electronic data security incidents in the last two years, in contrast to 65% of healthcare providers and payors. Nearly 60% of all [BA] participants said their incident response process had inadequate funding and resources, and the majority had not performed risk assessments.”
True, it’s the mega-breaches that have gotten the greatest press. Most recently, Advocate Health Care Network, which operates 12 hospitals and more than 200 other treatment locations in Illinois, settled with HHS on a $5.55 million penalty related to breaches that compromised the electronic data of 4 million patients. Though Advocate said there was no indication that the information was misused, HHS said the settlement was a result of “the extent and duration of the alleged noncompliance” by Advocate Health Care with HIPAA.
In other words, even if breached data is never sold or otherwise misused, entities covered by HIPAA regulations are subject to major penalties.
Which takes me back to business associates. Frankly, it’s hard to have much patience for the “mistakes” of covered entities like Advocate Health, all of whom should have known HIPAA requirements by heart for many years. But business associates? Many don’t yet have a clue about their responsibilities and their liability. A big reason is lack of diligence by their covered entity clients in requiring and enforcing BA agreements. So, a scenario exists where if a business associate commits a data breach and is penalized, their provider and payor clients could also be penalized.
Providers and payors need to home in on their business associates’ practices. These covered entities have Compliance Officers; BA agreements and enforcement are part of their jobs. They must ensure that their business associates diligently get on board with HIPAA — or replace them with more responsible vendors. Compliance Officers, get on their cases!
Here’s our latest HIPAA infographic to share as a reminder. Or, download here and send it to your business associates.
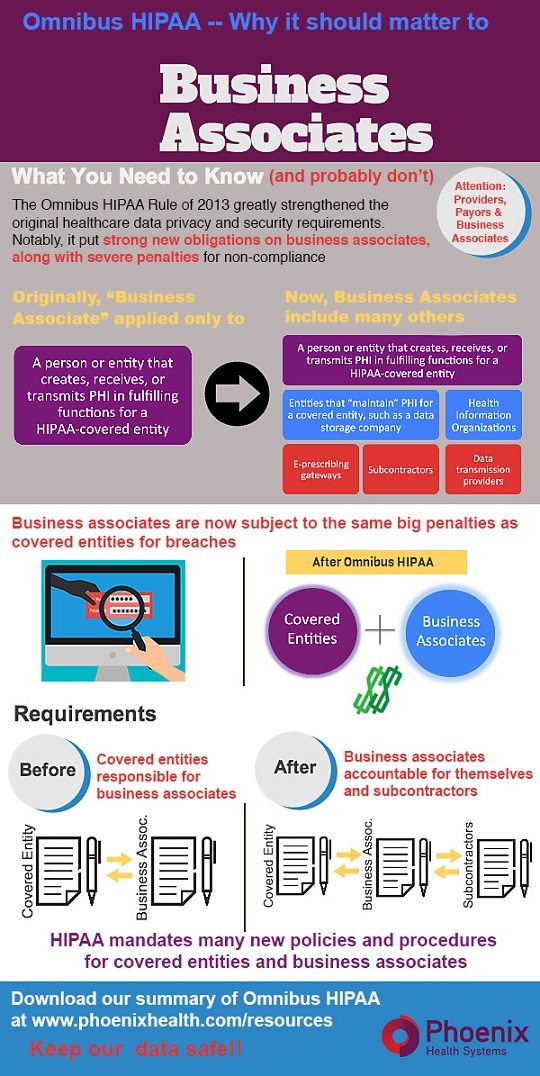
This article was originally published on Phoenix Health Systems and is republished here with permission.
